Transparent Data Encryption (TDE): Protecting Sensitive Data in Databases
Learn how to easily protect your data at-rest in a Microsoft SQL database environment.
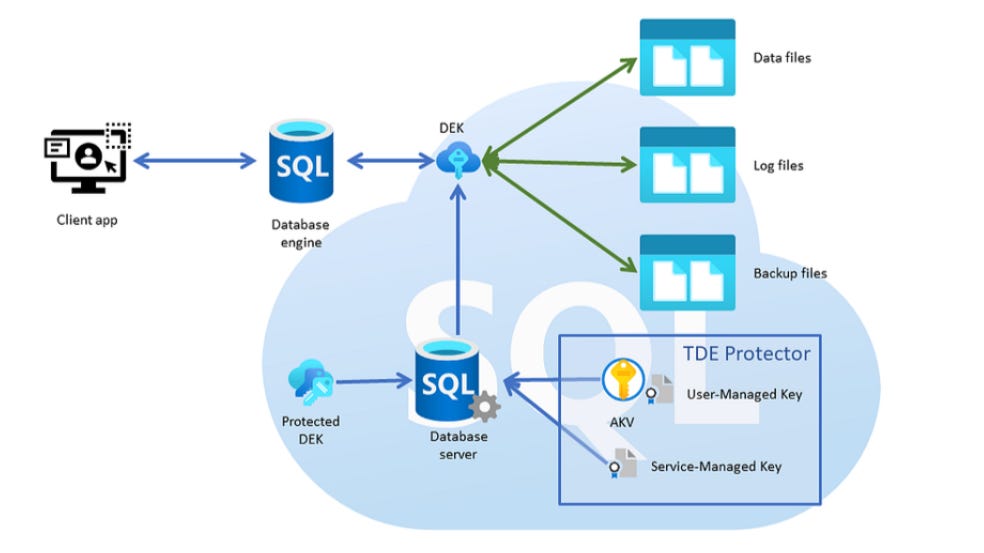
What is Transparent Data Encryption (TDE)?
Transparent Data Encryption (TDE) is a security feature used by many database systems to encrypt data at the storage level. By encrypting the data files and backups, TDE helps ensure that unauthorized users cannot view or access sensitive information even if they obtain access to the raw data files. TDE operates transparently to applications and users, meaning it encrypts and decrypts data automatically as it is read from and written to the disk.
The Importance of TDE in Today's Data Encryption Standards
Data breaches and unauthorized data access are significant concerns in the digital age. Regulatory frameworks like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) often mandate strong data protection practices, including encryption. TDE is a simple but effective measure for securing data at rest, allowing organizations to meet these compliance requirements while protecting data against physical theft and unauthorized access.
Using TDE aligns with data protection standards that emphasize data security, especially for businesses dealing with Personally Identifiable Information (PII) or other sensitive data. By encrypting data, TDE protects against data exposure risks in the event of lost, stolen, or compromised database files, which carry potential heavy financial and reputational damage.
TDE on Cloud Platforms: AWS and Azure SQL Databases
Major cloud providers like Amazon Web Services (AWS) and Microsoft Azure offer databases with TDE enabled by default:
AWS (Amazon RDS): For database engines such as Microsoft SQL Server and Oracle, AWS enables TDE by default for its Amazon RDS instances. This feature ensures that all data stored within RDS databases is encrypted at rest, providing a first layer of defense for sensitive information.
Azure SQL Database: In Azure SQL Database, TDE is also enabled by default. This automatic encryption helps Azure customers protect their data without needing to perform complex setup procedures. By incorporating TDE as a default, Microsoft simplifies the encryption process and allows organizations to meet data protection regulations more easily.
Having TDE enabled by default on these cloud platforms allows organizations to focus on other aspects of security and compliance. It is particularly valuable for industries like finance, healthcare, and retail, where managing sensitive information and PII is a routine part of business operations.
TDE and PII: Benefits for Organizations Handling Sensitive Data
Personally Identifiable Information (PII) includes data like social security numbers, addresses, and financial information that can uniquely identify an individual. For organizations that handle, store, or transmit PII, the risk of data breaches can have severe consequences, including regulatory penalties and a loss of customer trust.
TDE provides a critical layer of protection by:
Ensuring Data Confidentiality: Even if attackers gain access to the database files or backups, the data remains encrypted and unreadable without the decryption keys.
Meeting Compliance Requirements: Regulatory frameworks often require encryption for PII. TDE helps organizations fulfill these encryption mandates with minimal configuration effort.
Supporting Data Privacy: By encrypting data at the storage level, TDE helps protect PII from exposure due to physical theft, unauthorized access, or accidental loss.
Enabling TDE on a SQL Database: Step-by-Step Guide
Here’s how you can enable TDE on the AdventureWorks database in SQL Server. This example includes creating a certificate, backing it up, and then enabling TDE on the AdventureWorks database.
-- Step 1: Create a master key in the master database
USE master;
GO
CREATE MASTER KEY ENCRYPTION BY PASSWORD = '<<your_strong_password>>';
GO
-- Step 2: Create a certificate for TDE in the master database
CREATE CERTIFICATE AdventureWorksCert
WITH SUBJECT = 'TDE Certificate for AdventureWorks';
GO
-- Step 3: Back up the certificate and private key for recovery purposes
BACKUP CERTIFICATE AdventureWorksCert
TO FILE = 'your//backup//path//AdventureWorksCert.cer'
WITH PRIVATE KEY ( FILE = 'your//backup//path//AdventureWorksCert.pvk',
ENCRYPTION BY PASSWORD = '<<your_strong_password>>');
GO
-- Step 4: Create a database encryption key and protect it with the certificate
USE AdventureWorks;
GO
CREATE DATABASE ENCRYPTION KEY
WITH ALGORITHM = AES_256
ENCRYPTION BY SERVER CERTIFICATE AdventureWorksCert;
GO
-- Step 5: Enable Transparent Data Encryption (TDE) on the AdventureWorks database
ALTER DATABASE AdventureWorks
SET ENCRYPTION ON;
GO Verifying TDE Status
To verify TDE is enabled and operational, you can query the sys.dm_database_encryption_keys view:
SELECT DB_NAME(database_id) AS DatabaseName,
encryption_state,
key_algorithm,
key_length
FROM sys.dm_database_encryption_keys; Potential Impact and Considerations
While TDE offers seamless encryption for data at rest, there are some considerations to keep in mind:
Performance Overhead: Since TDE adds encryption and decryption operations as data is read from or written to disk, there may be a slight performance impact. However, this impact is typically minimal and may not be noticeable in most environments.
Backup and Restore: Restoring TDE-encrypted databases requires the encryption certificate and private key. It is crucial to back up these encryption artifacts securely; losing them will render the database backups unrecoverable.
No Application-Level Changes: TDE operates transparently to applications, meaning application code generally does not need modification. However, it’s important to ensure that applications interacting with the database understand the backup and recovery implications of TDE.
Encryption at rest for NoSQL instances such as MongoDB
MongoDB provides the following encryption methods:
Encryption at Rest:
Field-Level Encryption:
How MongoDB’s Encryption Compares to TDE
While MongoDB doesn’t label its encryption as “TDE,” the encryption-at-rest feature offers similar functionality by protecting the data stored on disk. Like TDE, MongoDB’s encryption at rest ensures that data stored in the database files is encrypted, protecting it from unauthorized access to physical storage or backups.
Managing Keys for Encryption in MongoDB
MongoDB allows you to manage encryption keys through various Key Management Services (KMS):
AWS KMS: You can manage keys for MongoDB's encryption at rest by integrating with AWS KMS, enabling secure key management practices.
Azure Key Vault and Google Cloud KMS are also supported, giving users flexibility based on their infrastructure.
Local Key Management is an option for on-premises deployments, though using a KMS is often recommended for improved security.
In summary Transparent Data Encryption is an essential security feature for any organization looking to protect its data at rest. By default, TDE is available in major cloud services such as AWS and Azure SQL databases, making it an accessible option for enhancing data security. For organizations that handle PII, TDE provides a crucial layer of protection, helping them meet regulatory requirements while reducing the risk of data exposure. When implemented alongside other security measures, TDE helps organizations safeguard their sensitive information and reinforce their data protection strategies. For projects utilizing data schema flexibility and modeling advantages by using NoSQL architectures, data-at-rest is still an option and should be used for the same reasons and purposes discussed here.